Technology Risk Assessment
Category: IT Security OIT - Categories Audience: Faculty Staff
Third-party vendor apps and cloud services can pose risks to the university. To reduce these risks, the Risk and Compliance (RAC) team reviews vendors handling confidential or highly confidential data, including HIPAA, FERPA, and PCI.
Get Started
Overview: Risk and Compliance (RAC) Process
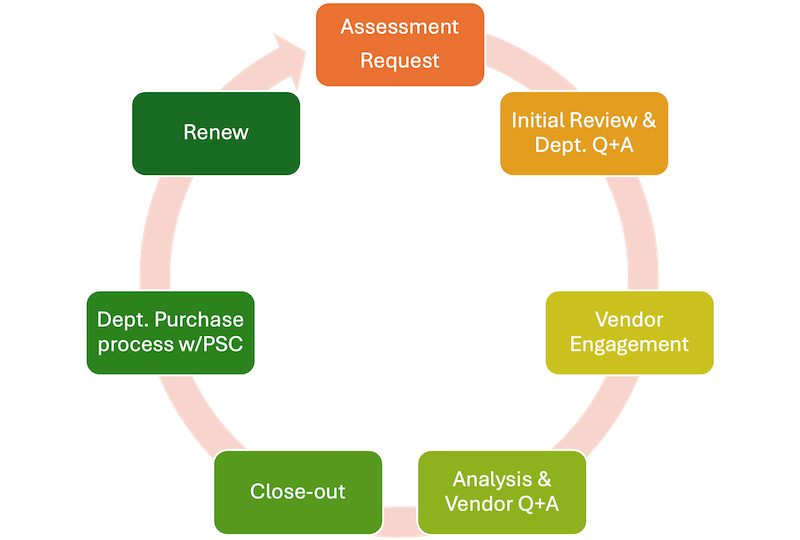
The Risk and Compliance process consists of the following steps:
- Assessment request is submitted
- An initial review and department Q&A
- The vendor will be engaged by the RAC team
- Analysis of the vendor-provided information, and vendor Q&A with RAC team
- Close out (approved, approved with conditions, denied)
- Requesting department will purchase the approved software/application with university procurement (PSC)
- Department will resubmit an assessment request when it is time to renew the software or application license (this could be annually or custom duration depending on the contract agreement)
Compliance Requirements
To protect university confidential and highly confidential data, including PHI, the RAC team assesses the security and practices of all third-party vendor server applications and cloud services.
Third party vendors must:
- Prevent the loss, theft, unauthorized access and/or disclosure of university data
- Destroy data when no longer needed per university data owner instructions
- Have incident response procedures and reporting requirements in case of a breach
Timeline
Requests are processed in order received. Timelines depend on responsiveness and complexity, typically taking 10–15 business days. More details are on the Technology Risk Assessment webpage (SSO required).
To get started, Complete the Technology Risk Assessment form.
Digital Accessibility
The RAC process includes working with vendors to ensure that technology procured by the university is inclusive and accessible. The RAC process collects a Voluntary Product Accessibility Template (VPAT) and accessibility questionnaire from the vendor to produce a digital accessibility risk assessment. For reference, visit our CU Anschutz Procuring Accessible IT guide.This assessment provides insight into the technology's digital accessibility level of compliance and is sent back to the original requestor.
Other University Teams to Contact for Process
- Procurement Service Center (PSC) - The team that will assist you with your purchase.
- Procurement Service Center - Existing CU Price Agreements
- Data Integration Requests - If your request will include the integration of your software with CU System to retrieve university data, enter a data integration request as soon as possible.
- Office of Regulatory Compliance (ORC) - If your request involves HIPAA data, the Office of Regulatory Compliance will be asked by the PSC to prepare a BAA for both parties to sign.
Resources
- In-depth Technology Risk Assessment Process
- University Data Classification
- University Adverse Impact Level
- IT Security Program APS-6005
- University HIPAA Policy
- FERPA - Student Data Use Guidelines
- PCI
- Approved University Applications
- Vendor Requirements
- CU Digital Accessibility Vendor Procurement
- Colorado Accessibility Law
- CU Anschutz Digital Accessibility
- Digital Accessibility and Colorado Law HB21-1110
- CU Anschutz Procuring Accessible IT guide.